Data Collection Methods
The following sections describe the most common data collection methods. In some cases, you'll need to provide the directory or file location where the Collector can access the server logs. You can specify a local folder path or a Windows UNC (Universal Naming Convention) path to a hosted network drive.
Only those log entries that are added to the file after the Event Source is connected to a Collector are uploaded to InsightIDR.
Watch directory
The watch directory is the network location of a watch directory where log files are copied. This method monitors a specified directory on a local or remote host and uploads files added to the directory, at 30-second scan intervals. Use this method for log files that roll over to new files, for example, Microsoft DHCP and IIS (Internet Information Services) log files.
Tail file
This is the network location of a tail file where log data is stored. This method watches a specific file written to disk using the equivalent of the UNIX tail command, at 20-second scan intervals. Use this method for log files that are written continuously to a single file, for example, Windows DNS log files.
Listen for Syslog
The TCP or UDP port where syslog events are being forwarded. Many network appliances can be configured to deliver audit logs over syslog to a server. These appliances should be configured to send their logs to a unique port on the Collector where an Event Source has been set up in InsightIDR to ingest the logs. Collectors accept syslog messages over UDP or TCP.
SIEM
In some deployments, a SIEM may already collect data. You can configure your SIEM to send logs to the Collector by selecting the appropriate SIEM under Log Aggregator when configuring the Event Source in InsightIDR.
Honey Pots
A Honey Pot is a virtual server that you can deploy on your network from InsightIDR. Honey Pots are fake assets that produce an alert any time a user attempts to connect to the device. Once attackers find an initial foothold in a network, their next step is typically a network scan to identify all the other assets in the network. The Honey Pot provides a simple way to detect attackers from attempting to scan your network.
If your organization uses a naming convention for assets and/or users, configure these intruder traps to match all naming conventions; do not name your Honey Pot honeypot, or your honey user John Doe. If an attacker is smart enough to get past perimeter defenses, then he’s smart enough to avoid obviously fake assets and users.
We also recommend deploying both Honey Pots and honey users throughout the environment with an added emphasis on critical network segments or subnets. In the event of a breach, having tiers of intruder traps can help isolate the precise location of an intruder or malicious insider in the network, helping Incident Response teams lock down users and assets quickly to contain the incident.
Deploying a honey pot
- On the Collectors page, click Download Collector and select Honeypot (OVA).
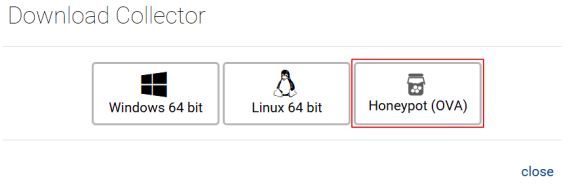
- Download the Honey Pot.
- In your VMware environment, create a new VM from the OVA.
- Power on the VM. You will see the following prompt:
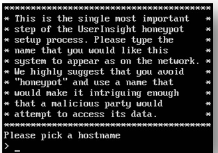
- Provide a name that fits your network naming convention and makes the machine look important.
- Acknowledge the machine's IP address when you are prompted.
- Continue until you see the following:
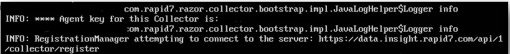
- Take note of the Agent key (xxxxxxxx-xxxx-xxxx-xxxxxxxxxxxx) that is displayed.
- On the Collectors page, click Activate Collector.
- Enter a name for the Honey pot and enter the Access Key to pair the Honey Pot OVA to your InsightIDR instance.
Once paired successfully, you will receive automated alerts of any time an attempt to the Honey Pot is made, a standard discovery scan is run, a vulnerability scan run, an exploit occurs or an attempt to brute force the Honey Pot happens. These are all common techniques during the reconnaissance and enumeration phase of the attacker’s kill chain.
Creating a Honey User
- Create a new user in Active Directory with a believable name, but don’t give anyone access to the account. This will be your new honey user.
- Give the honey user every appearance of a normal employee of the company. This includes things like a complex passphrase, organizational mappings, permissions, or whatever else may trick an attacker into believing the user is an actual employee.
- Remember that honey users can have multiple accounts. In fact, multiple accounts can increase the likelihood that an attacker will target the user, as it seems more authentic and provides additional chances for reaching an administrative role (or so the attacker thinks).
- Log in to your account in InsightIDR. Select Settings --> Honey Users and enter the newly created hone user's name in the search bar. Select the name to mark the user as a Honey User.
Endpoint Monitor
The Endpoint Monitor is a unique Event Source in the InsightIDR Collector infrastructure in that it acts as a scanner to query endpoints across the network. The Endpoint Monitor technology ingests this information into InsightIDR without requiring an agent to be installed on the endpoints themselves.