Linked and Shared Accounts
When any user logs into their local system or a remote system with a different account than their current account, that account switch - which Microsoft describes as an impersonation - is recorded on the endpoint. All impersonations are reported back to InsightIDR via the Endpoint Scan, where they are presented as Linked Accounts or Shared Accounts.
A linked account is an account association where InsightIDR has observed one and only one other account authenticating as the target account. A typical example of a linked account is when an administrator logs into their domain admin account in order to perform some administrative activity. As long as no other users use that domain admin credential, the low-privilege user and the admin user are presented as a pair on the Linked Accounts page.
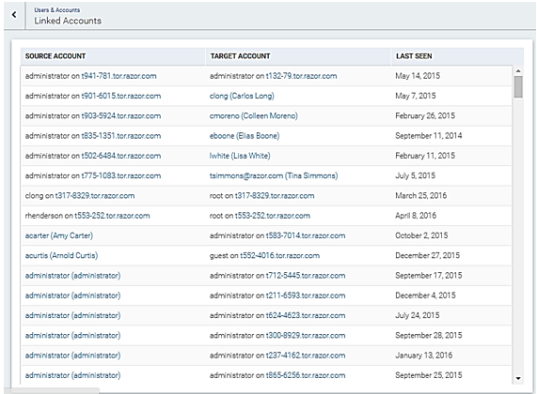
An account moves from linked to shared when more than one user is witnessed authenticating with the target account’s credentials. Shared accounts are considered a yellow flag. These accounts might be examples of users sharing their credentials or even a compromised user’s account getting used by an attacker as a jumping point to other accounts as the attacker moves laterally across the network.
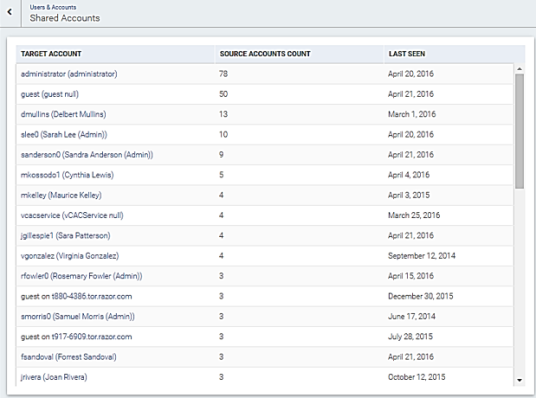
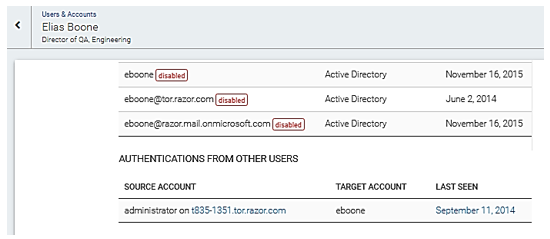
Any account that has been used to log on to the target account can be reviewed on the Shared Accounts page or on the user details page for the target account.
Local accounts
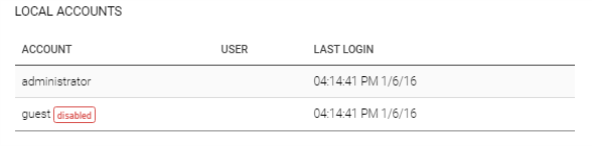
Any local accounts on an endpoint become visible as a result of the Endpoint Scan. Local accounts for an asset are presented on that asset’s details page, and lateral movement from asset to asset using local accounts - a common attack vector for infiltrators to cross a compromised network without informing the Active Directory - are displayed on the lateral movement graph for each asset.
What's Next?