Adding Nexpose and Metasploit Event Sources
If you currently are a Metasploit or Nexpose user, you can add them as event sources to your collector.
Adding Nexpose as an event source
Integrating with Nexpose lists the vulnerabilities on your network, ordered by the number of users impacted by the vulnerability.
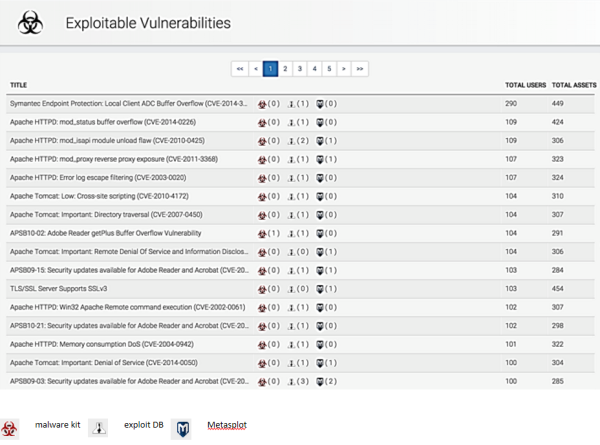
Every asset that has been scanned by Nexpose displays its vulnerabilities in InsightIDR.
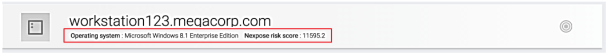
Scanned assets also display their OS type and Nexpose risk score below of the asset details page.
To add Nexpose as an event source to your Collector, you must have the administrator account information username and password for the Nexpose server.
To add Nexpose as an event source:
- Go to Data Collection > Set up Event Source > Add Event Source.
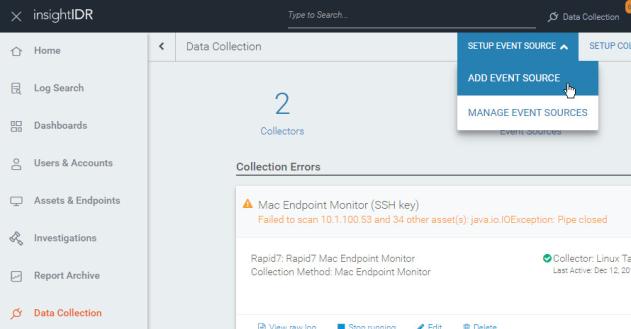
- From the "Add Event Source" page, find the Rapid7 section and select Nexpose.
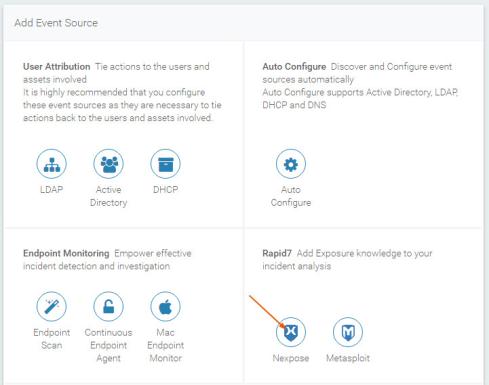
- From the "Add Rapid7 Event Source" page, enter a name for the Nexpose event source in the Display Name field.
- Select the appropriate time zone of the Nexpose server from the Timezone dropdown menu.
- Enter the server name of the Nexpose server in the Server field.
- Enter the port number of the Nexpose server in the Port field. The default port is 3780.
- Select the credential from the Credential dropdown menu.
- Enter the administrator's username in the Username field.
- Enter the administrator's password in the Password field.
- Enter the number of hours you want to poll the event source in the Polling Rate field.
- Save your changes.
Adding Metasploit Pro as an event source
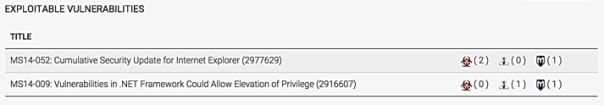
InsightIDR integration with Metasploit is tied to Metasploit social engineering campaigns. When customers launch a social engineering campaign in Metasploit and they have integrated the tool with InsightIDR, the InsightIDR User Details page provides a tracker on how the user has performed in the campaign. The tracker shows how vulnerable the user would have been in this Metasploit social engineering campaign. Metasploit can generate multiple social engineering campaigns.
Metasplot tracks the following for each user in social engineering campaigns :
- They received the email.
- They opened the email.
- They clicked on the link.
- They provided their credentials on the social engineering site.
Generating an API key in Metasploit Pro
Before you can add Metasploit Pro as an event source, you'll need to generate an API key. You'll need it to configure the event source.
To generate an API key in Metasploit Pro:
- Log in to Metasploit Pro.
- Hover over Administration in the top right hand corner to display the Administration menu.
- Select Global Settings.
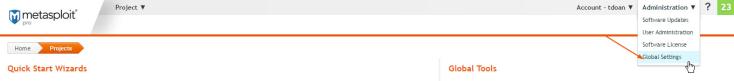
- Scroll down the Global Settings page to the Authorized API Keys section.
- Click on Create an API Key.
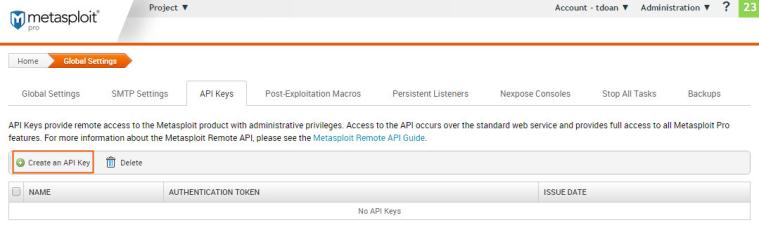
- Enter a name for the key.
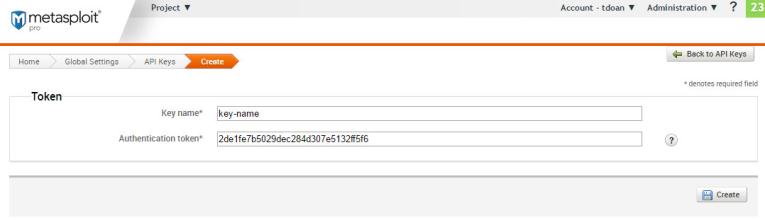
- Create the key.
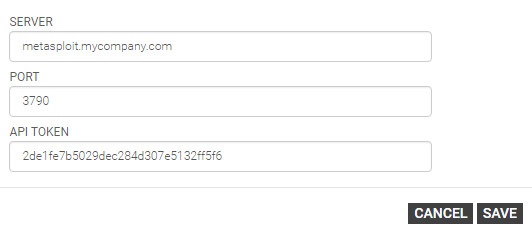
Adding Metasploit Pro as an Event Source
- Go to Data Collection > Set up Event Source > Add Event Source.

- From the "Add Event Source" page, find the Rapid7 section and select Metasploit.
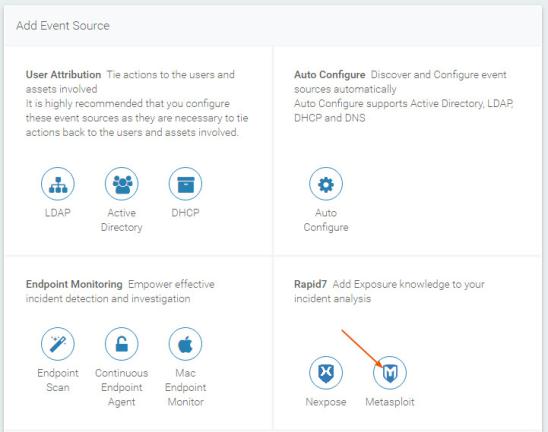
- Enter a display name in the Display Name field.
- Select your time zone from the Timezone drop-down menu.
- Enter the server address running Metasploit in the Server field.
- Enter the port number in the Port field. The default port is 3790.
- Enter the API Token that you previously generated in the API Token field.
- Save your changes.