Getting Logs from a Check Point Device with OPSEC LEA
The Open Platform for Security (OPSEC) Log Export API ( LEA) provides the ability to pull logs from a Check Point device based on the OPSEC SDK. OPSEC LEA listens on port tcp/18184 on the device (OPSEC LEA Server) which contains your logs. Your OPSEC LEA Client then connects into 18184 and pull the logs.
You need to make sure port tcp/18184 is allowed on the firewall or the smart center conf file as it is disabled by default.
Setting up the checkpoint
- Create an OPSEC LEA Object within the OPSEC LEA and Applications tab.
- From the dashboard go to Manage>Servers and OPSEC Applications.
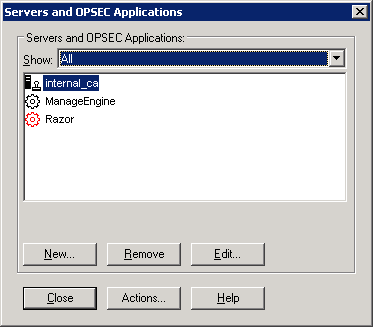
- Click the New button.
- Choose OPSEC Application from the New drop-down menu.
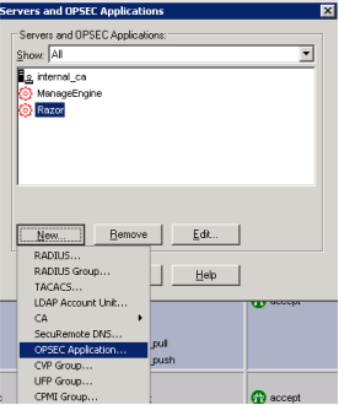
- In the OPSEC Application Properties dialog, enter InsightIDR in the Name field.
- Under Application properties, leave the Vendor field as User defined.
- Tick LEA from the Client Entities list.
- In the Host Node dialog, enter InsightIDR-Collector in the Name field.
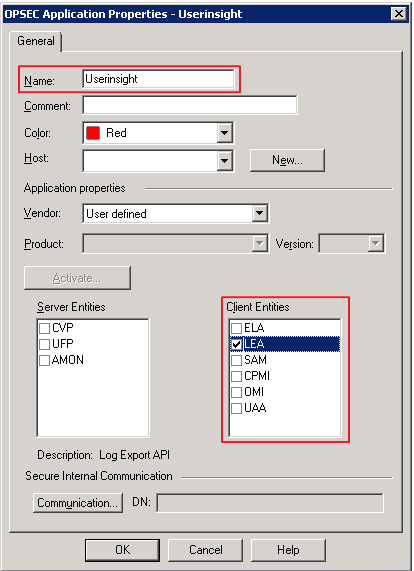
- Enter the IP address in the IP Address field.
- Click the OK button to save the host creation.
Setting up a password for the Collector to authenticate to the checkpoint
In the OPSEC configuration properties, click Communication. You need to set up a one-time password for the Collector to authenticate to Checkpoint.
- Enter your password in the One-time password field.
- Re-enter your password in the Confirm One-time password field.
- Click the Initialize button.
- Click the Close button.
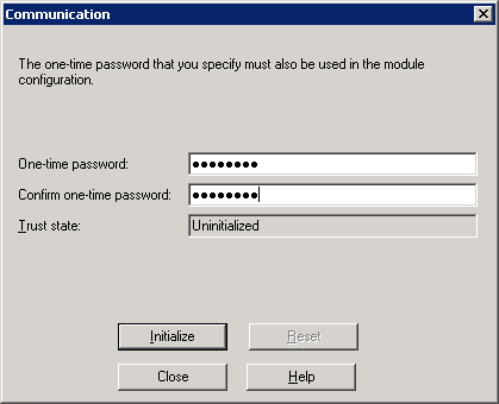
Once you create your password, the Trust state field displays the trust state as Initialized but trust not established. It becomes established when communication has been established from the Collector to the checkpoint firewall.

Identifying the DN of the object
The OPSEC Application is created. You may need to identify the DN of the object. To do this:
- Highlight the object.
- Click the Edit button.
- Take note of the DN.
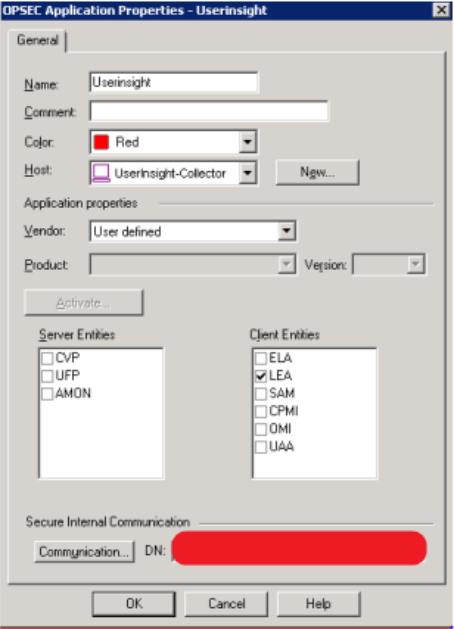
Save the configuration and install database in case of Smartcenter or Provider1. If you are directly collecting from the firewall, you will need to add a rule in your rule base to allow the Collector to connect to the firewall over port tcp/18184.
Exporting the certificate
The command line tools allow you to incorporate the OPSEC server certificate into (Undefined variable: Variables.Project) allowing the two systems to communicate.
opsec_pull_cert.exe -h host -n name -p password [-o output file]
Referring to the previous command, substitute:
- host with address of the Checkpoint server
- name with file name used in the previous step (see the previous screen capture)
- password with your password
- output file with opsec.p12
Here is the command line with the appropriate parameters.
opsec_pull_cert.exe -h 10.100.100.101 -n file name used in previous step
-p MyOneTimePassword -o opsec.p12
After exporting the file, move it to the following directory on the Windows machine running the (Undefined variable: Variables.Project) Collector:
- C:\{InsightIDR Installed Directory}\checkpoint-config\{Application Name}\
where Application Name matches the name argument from the opsec_pull_cert.exe command.
Restart the event source to load the certificate into the Collector.
Enabling the LEA server
Perform the following steps to enable the LEA server to allow the firewall to talk to the Collector. This is disabled by default. You need to edit the fwopsec.conf file which resides in the $FWDIR/conf directory on Linux, or which resides in the %FWDIR%\conf\ directory on Windows.
- Locate the following lines:
#lea_server auth_port 18184#lea_server port 0 - Change the lines to the following (if the lines are missing, add them to the file):
lea_server auth_port 18184lea_server auth_type ssl_opsec
Installing the Visual C++ Redistributable
If the event source fails with the error message Checkpoint LEA Engine terminated unexpectedly, extra files need to be installed on the machine running the Collector to support the Checkpoint event source.
These files can be downloaded from http://www.microsoft.com/en-us/download/details.aspx?id=30679.
You'll need to select the vcredist_x86.exe file even though the Collector is a 64-bit system.
Install the additional DLLs and restart the computer. The Checkpoint event source should now be able to connect to the Checkpoint firewall.
Directly invoking the checkpoint executable
If the Checkpoint event source continues to experience errors, invoke the executable responsible for connecting to Checkpoint directly. This executable will be found in one of the higher numbered bundles under the felix-cache directory: C:\{UserInsight installed directory}\felix-cache\bundle{XX}\data\opsec\checkpoint-lea-win-exe.exe where {XX} is a high numbered bundle in your felix-cache directory that has the opsec subdirectory inside of it.
The executable needs to be invoked with a number of parameters to connect to the Checkpoint server:
C:\{UserInsight installed directory}\felix-cache\bundle{XX} \data\opsec\checkpoint-lea-win-exe.exe "lea_server" "{application SIC name}" "{path to certificate file}" "{Checkpoint address}" "{Checkpoint port}" "sslca" "{server SIC name}" "1"
For example, substituting these:
- {UserInsight installed directory} with C:\Program Files\rapid7\UserInsight
- bundle{XX} with bundle45
- {application SIC name} with CN=UserInsight,O=fwmgmt.myorg.org.ab12cd
- {path to certificate file} with C:\Program Files\rapid7\UserInsight\checkpoint-config\UserInsight\opsec.p12
- {Checkpoint address} with 10.100.100.101
- {Checkpoint port} with 18184
- {server SIC name} with cn=cp_mgmt,o=fwmgmt.myorg.org.ab12cd
would result with the following command:
C:\Program Files\rapid7\UserInsight\felix- cache\bundle45\data\opsec\checkpoint-lea-win-exe.exe "lea_server" "CN=UserInsight,O=fwmgmt.myorg.org.ab12cd" "C:\Program Files\rapid7\UserInsight\checkpoint-config\UserInsight\opsec.p12" "10.100.100.101" "18184" "sslca" "cn=cp_ mgmt,o=fwmgmt.myorg.org.ab12cd" "1"
If the EXE returns with no errors, look for the opsec-debug.log file in the same folder as the checkpoint executable. This file contains detailed diagnostics of the error.
If the file contains the following error::
[OpsecDebug]PM_session_init: given session O(CN=UserInsight,O=fwmgmt.myorg.org.ab12cd;cn=cp_mgmt,o=fwmgmt.myorg.org.ab12cd;18184;lea).
[OpsecDebug]PM_policy_query: input session O(CN=UserInsight,O=fwmgmt.myorg.org.ab12cd;cn=cp_mgmt,o=fwmgmt.myorg.org.ab12cd;18184;lea).
[OpsecDebug]PM_policy_query: rule found (ME;cn=cp_mgmt,o=fwmgmt.myorg.org.ju2ahc;18184;lea;sslca(1/1)).
[OpsecDebug]PM_policy_query: finished successfully. 1st method = sslca
[OpsecDebug]PM_policy_choose: finished successfully. choose: DENY.
[OpsecDebug]policy_choose: choose failed.
[OpsecDebug]sic_client_negotiate_auth_method: policy choose failed.
[OpsecDebug]fwasync_mux_in: 360: handler returned with error
[OpsecDebug]sic_client_end_handler: for conn id = 360
[OpsecDebug]opsec_auth_client_connected: connect failed (119)
Update the fwopsec.conf file described on page 13 to use the auth_type ssl_ca, after which the file will read:
lea_server auth_port 18184
lea_server auth_type ssl_ca