Active Directory (AD) Domain Controller Event Sources
Microsoft Active Directory integration is critical for InsightIDR. InsightIDR listens for Windows Security Event Logs for critical information that is used to generate incidents and become a source of data for investigations.
InsightIDR can ingest Microsoft Active Directory Security logs by:
- Making WMI calls from the collector.
- Listening for Syslog.
- Listening for logs forwarded from a log aggregator.
Configuring Active Directory (AD)
- Under the Active Directory tab on the Collectors page, click the Add event source button.
- Select Microsoft Active Directory Security Logs from the Event Source drop-down menu.
- Select your Collection Method.
- Listen For Syslog requires a syslog server to send event logs over a predefined port.
- Log Aggregator requires a SIEM tool to send event logs over a predefined port.
AD Domain Controllers do not mirror data – repeat steps 1-3 for each DC in your environment.
Adding Active Directory as an Event Source
- Go to Data Collection > Set up Event Source > Add Event Source.
- From the "Add Event Source" page, find the User Attribution section and select Active Directory.
- From the "Add Active Directory Event Source page," click the Event Source dropdown menu and choose Microsoft Active Directory Security Logs.
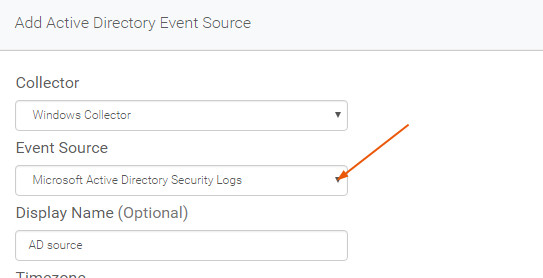
- Enter a name for the Active Directory event source in the Display Name field.
- Select the appropriate time zone from the Timezone drop-down list.
- Click the WMI button for the Collector Method.
Note: WMI requires access via an admin account and communication over ports 135, 139, and 445.
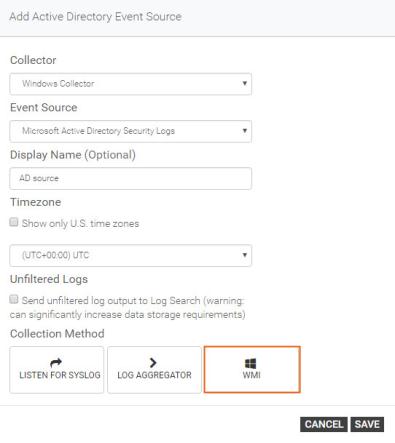
- Enter the Fully Qualified Domain Name (FQDN) of the domain controller in the Server field.
- Provide the user domain.
- Enter the server name in the Server field.
- Enter the user domain in the User Domain field.
- Select the appropriate credential type from the Credential drop-down list.
- If you are adding a new credential, you'll need to provide the username and password that will be used. The credentials must have administrator privileges.
- Save your changes.
Troubleshooting issues with setting up an Active Directory event source
In rare circumstances, AD domain controllers may be configured to not support WMI. In this case, you can use the following to troubleshoot if WMI access is available.
Test WMI rights
The first thing you want to try is test the WMI rights.
- Run wmimgmt.
- Right-click WMI Control (Local).
- Click Properties, then the Security tab.
- Open root and highlight CIMV2.
- Click Security and confirm the following rights:
- Execute Methods
- Enable Account
- Remote Enable
If a WMI browsing tool is available, from the collector machine, you should now be able to connect and browse cimv2. If you do not have a WMI browser, you can skip this testing step and obtain one only if further troubleshooting is needed.
Test DCOM
- Run dcomcfng.exe.
- Under Component Service, open Computers and right-click My Computer.
- Click Properties and then the COM Security tab.
- Under Launch and Activation Permissions, click Edit Limits.
- Confirm Remote Launch and Remote Activation.
Review WMI logs
The WMI logs are extremely useful and detailed. They can be found under the Event Log, in Applications and Services Logs/Microsoft/Windows/WMI Activity.
If you continue to get errors with the collector about not being able to read time or similar issues, it is likely a WMI permission issue. The collector logs combined with the WMI logs on the server make it pretty easy to pinpoint missing WMI permissions.
Snare
If WMI is not working, you can install an open source tool like Snare to listen to the security logs of the AD servers and forward them to the collector over a syslog port: http://sourceforge.net/projects/snare/.