Setting Up Honeypots
Honeypots are one type of an intruder trap. InsightIDR provides a simple production Honeypot that you can deploy on their network to easily detect intruders. Customers can download the Honeypot open virtual appliance (OVA) from within InsightIDR from the Collectors page.
Downloading the honeypot
- Save the Honeypot OVA once the download completes.
- Begin the installation process.
- Ensure that the Honeypot can get a DHCP lease. Static IP addresses are not currently supported for the Insight Platform Honeypot (OVA).
- In your VMware environment, create a new VM from the OVA.
- Power on the VM. You will see the following prompt:
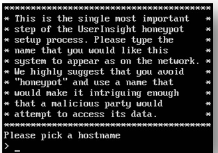
- Provide a name that fits your network naming convention and makes the machine look important.
- You will be prompted to acknowledge the machine’s IP address. Continue until you see:
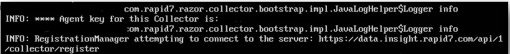
- Take note of the Agent key (xxxxxxxx-xxxx-xxxx-xxxxxxxxxxxx) that is displayed
- On the Collectors page in the InsightIDR web interface, click Activate Collector. Enter a name for the honeypot and enter the Access Key to pair the honeypot OVA to your InsightIDR instance.
- Once paired successfully, you receive automated alerts to any connection attempts to the honeypot; run a standard discovery scan, a vulnerability scan, throw some exploits, or attempt to brute force the honeypot to trigger an incident! These are all common techniques during the reconnaissance and enumeration phase of the attacker’s kill chain.
Honeypot incident alerts
- Click Incidents to display the Incidents page.

- From the left-hand panel, click Network Monitoring.
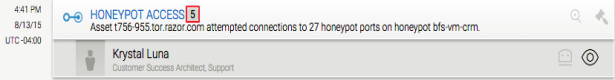
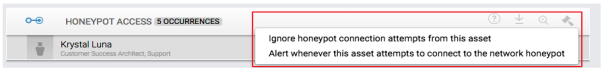
- An incident alert displays when the Honeypot is triggered. The number after the title HONEYPOT ACCESS designates the number of attempts the Honey User made.
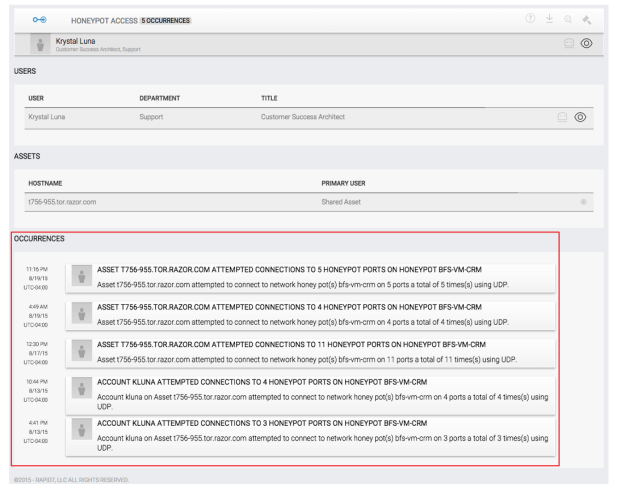
- Click on the incident alert to display a list of all the incident's occurrences.
- Click on an occurrence to display the Evidence panel.
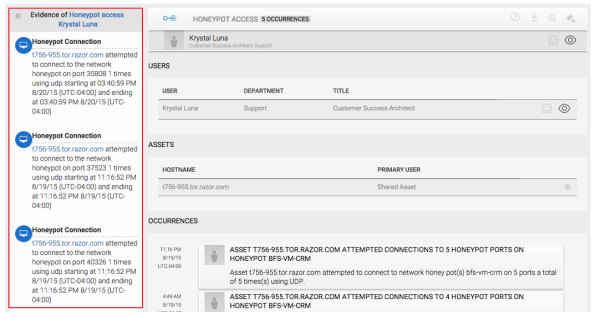
- Click on the gavel icon to close the incident after you assess the impact and validity of the Honeypot alert. You may either whitelist (ignore) or blacklist (alert) the incident for future Honeypot incident alerts.
Honey Users Overview
Honey Users are another type of intruder trap. They are legitimate looking accounts that should not actually be used. InsightIDR alerts on any activity associated with Honey Users.
The goal when creating Honey Users is to make them appear as real as possible. So, you'd want to:
- Create Honey Users in your Active Directory.
- Create user names that appears like real names.
- Create Honey User passwords that meet your password requirements.
Marking a user as a Honey User
- Click Settings.

- Click Honey Users in the Incident Settings panel on the left-hand side of the page.
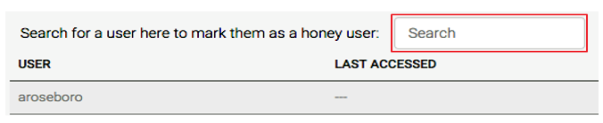
- Search for the name of the user who you want to designate as a Honey User.
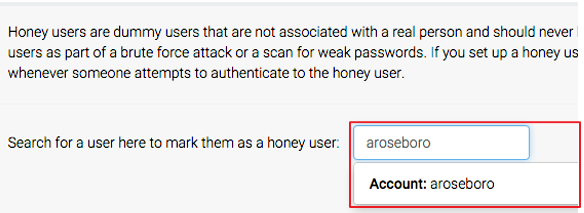
- Click on the name of a Honey User to display more information.
- You can export the Honey User information to a PDF, mark the user as a service the account, or place the user on the Watchlist.