Adding FireEye NX Logs to a Collector
FireEye NX Network Security helps you detect and block attacks from the web. It protects the entire spectrum of attacks from relatively unsophisticated drive-by malware to highly targeted zero-day exploits. Its capabilities provide an extremely low false positive rate by leveraging the FireEye Multi-Vector Virtual Execution (MVX) engine to confirm when malware calls out to C&C servers.
This document explains how to deliver logs from the FireEye NX appliance to an InsightIDR Collector.
Configuring FireEye NX to forward alert logs to InsightIDR Collector
- Log onto the FireEye NX Web.
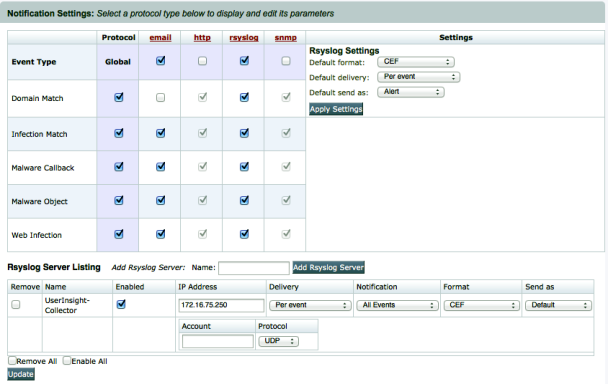
- Go to Settings | Notifications.
- Tick rsyslog to enable a Syslog notification configuration.
- Enter a name to label your FireEye connection to the InsightIDR Collector in the Name field.
- Click the Add Rsyslog Server button.
- Enter the InsightIDR Collector IP address in the IP Address field.
- Tick the Enabled check box.
- Select Per event in the Delivery drop-down list.
- Select All Events from the Notifications drop-down list.
- Select CEF as the Format drop-down list. Other formats are not supported.
- Leave the Account field empty.
- Select UDPfrom the Protocol drop-down list.
- Click the Update button.
Adding an event source
- Go to Data Collection > Add Event Source.
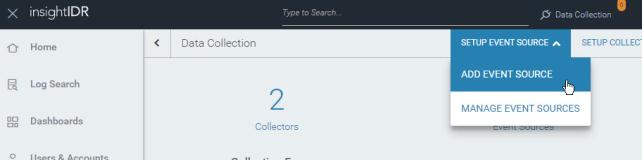
- When the Add Event Source page appears, find the Security Data section and select Advanced Malware.
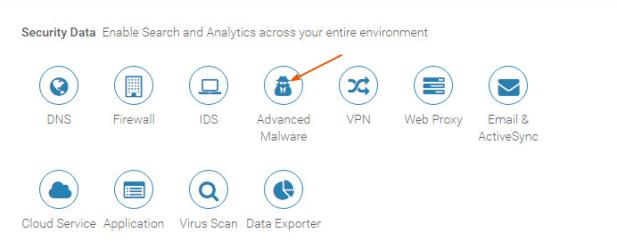
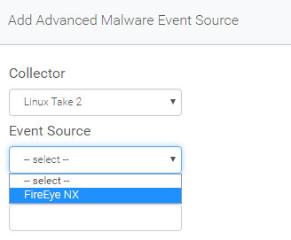
- From the Event Source dropdown menu, select FireEye NX from the Event Source.
- Enter a display name in the Display Name field.
- Set a time zone from the Timezone drop-down list.
- Click the Listen for Syslog button.
- Select UDPfrom the Protocol dropdown menu.
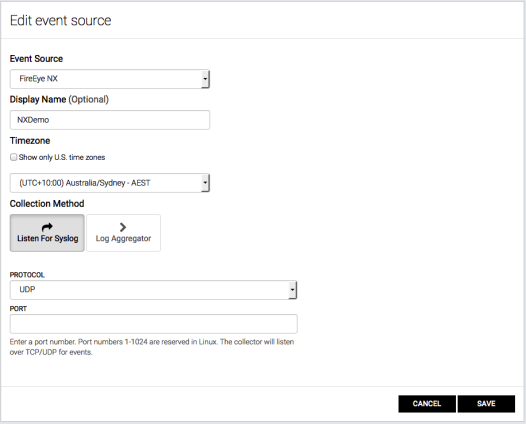
- Enter a port number in the Port field. FireEye NX uses port 514 by default. This can be changed from the command line interface. InsightIDR recommends that you do not use port 514 whenever possible. Use this port only for network systems that can't be configured to use any other port but port 514.
- Click the Save button.
Confirming the integration
Test that the FireEye NX Notifications page does not get sent to the InsightIDR Collector. To accomplish this, you need to trigger a real alert or use the deployment checks.
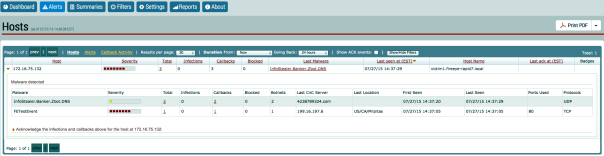
Confirming alerts in InsightIDR
- Confirm that the event shows up within a minute or two. You should see new incidents in the InsightIDR dashboard.
- Click the Incident to drill down into the event to display the User Context and Asset names.
- Click the ADVANCED MALWARE ALERT link to drill down to display the occurrences for this alert.
Troubleshooting
- Check the Collector log located at C:\\Program Files\Rapid7\logs\collector.log.
- If the FireEye NX log data is not visible in the (Undefined variable: Variables.Project) cloud, you should:
- Stop the FireEye NX event source.
- Create a Generic Syslog Listener on the same port. This is found under the Rapid7 category of event sources.