Before You Deploy InsightIDR
InsightIDR combines the full power of endpoint forensics, log search, and sophisticated dashboards into a single solution. It is an on-premise Software as a Service (SaaS) tool that collects data from your existing network security tools, authentication logs and endpoint devices and aggregates the data at an on-premise collector. The Collector filters out any sensitive data, such as personally identifiable information, from the logs and transmits them securely to AWS, where customer databases and the web interface are hosted. Rapid7 then runs analytics on this data to correlate users, accounts, authentications, alerts, and privileges, to provide you with insight into the behavior of each user in your environment, while also looking for known indicators of compromise.
You will need to have dedicated Collectors on-premise to collect event/log data. These Collectors can also be used to collect endpoint data if desired; however, Collectors do not collect endpoint data in real-time. For real-time endpoint data collection, you should also plan to install agents, called Continuous Agents, to your endpoints.
InsightIDR Architecture
InsightIDR features the ability to run endpoint forensics, log search, and run reports.
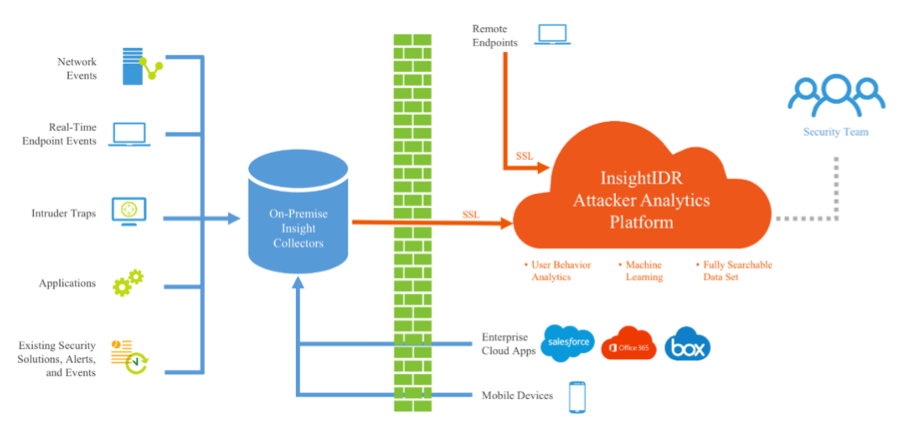
InsightIDR Predeployment Checklist Summary
This section contains a summary of the prerequisite steps that need to be completed for your InsightIDR deployment. More details regarding each step follow this section.
| Task | Who Needs to Complete this Step | Additional Information |
|---|---|---|
| Configure a dedicated host system to be used as a collector | Required for all deployments | You must complete this step before your scheduled deployment call. |
| Plan for Continuous Agents | Recommended for all deployments | We recommend that you choose a few endpoints on which to install the agent before the first deployment call. |
| Prepare service account (s) | Required for all deployments | You must complete this step before your deployment call. |
| Prepare for Log Collection – either forward logs from a SIEM OR prepare each event source for log collection | Can be done during the first day of deployment | Please read through the requirements for your log sources. If your organization requires you to complete any change controls or other activities before the deployment, be sure you have done those before your first deployment call. |
| Gather network information | Required for all deployments | We recommend that you have the information before the first deployment call, but it can be added later if needed. |
| Prepare for intruder trap setup | Optional for all deployments | This step is optional. |
| Prepare for Nexpose and Metasploit Pro integration | Optional and can be completed on the first day of deployment | This step is recommended for Nexpose and Metasploit Pro customers. |
| Access the Insight Platform | Required for all deployments | We recommend you test logging into your Insight cloud instance before the first deployment call; however, this can be done at the start of the call. |
| Download the Insight documentation | Optional | This step is optional. |
*If you will be forwarding logs from a SIEM, be sure you have read the SIEM documentation before the deployment call and completed any necessary preparation so that you will be able to begin forwarding logs on the first day of the deployment.
Ports used by InsightIDR
The table below outlines the necessary communication requirements for InsightIDR. Assess your environment and determine where firewall or access control changes will need to be made.
| Source | Destination | Port |
|---|---|---|
| All deployed collectors | data.insight.rapid7.com (US) or eu.data.insight.rapid7.com (EMEA) | 443 |
| All deployed collectors | s3.amazonaws.com (US) or s3.eu-central-1.amazonaws.com (EMEA) | 443 |
| All deployed collectors | endpoint.ingress.rapid7.com (US) or eu.endpoint.ingress.rapid7.com (EMEA) | 443 |
| All endpoints | Collector | 5508, 6608, 20000-30000 |
| All contiguous agents | Collector | 5508, 6608, 20000-30000 |
| Collector | Domain controller configured as LDAP source for LDAP event source | 636 |
| Collector | All domain controllers | 135, 139, 445 |
| Non-MS DHCP server | Collector | *UDP/TCP port above 1024 |
| Firewall | Collector | *UDP/TCP port above 1024 |
| Checkpoint Firewall | Collector | 18184 or other as specified |
| VPN | Collector | *UDP/TCP port above 1024 |
| AV Server (sending logs using syslog) | Collector | *UDP/TCP port above 1024 |
| Nexpose | Collector | 3780 |
| Metasploit | Collector | 3790 |
| box.com logs, Collector | https://api.box.com | 443 |
*The port specified must be unique for the Collector that is collecting the logs
What's Next?