Reusing Credentials
With exceedingly more and more stringent password requirements, credential reuse is becoming a common issue within many organizations. Users inundated with complex password policies may resort to reusing the same password across multiple accounts so that they can easily manage their credentials. This can cause major security issues when those credentials are compromised. For example, if an attacker is able to obtain valid credentials on one target, they can try those credentials on other targets to further compromise the network.
To help an organization audit their passwords, you can reuse credentials to identify additional targets that will be vulnerable if a particular credential is compromised. Credentials Reuse is a Metasploit Pro feature that reuses validated credentials to attempt to authenticate to additional targets. This feature is useful when you have validated or known credentials that you want to try on a set of targets. For example, if you were able to obtain an NTLM hash on a target, you should try to reuse that hash on other SMB targets. If a system administrator commonly deploys the default configuration for a system, the likelihood that the credential will work is high.
Credentials Reuse Workflow
Credentials Reuse provides guided workflow for the required tasks that need to be configured. Each task in the workflow is displayed on its own tab. You can click on any of the tabs to switch between the different tasks in the workflow; however, you must complete each task before you can move to the next.
The Credentials workflow is shown below:
The workflow is quite simple and comprises of four steps:
- Select the targets that you want to try the credentials on.
- Select the credentials that you want to use to authenticate to the selected targets.
- Configure the reuse settings, such as the timeout and validation limits, and review the target that you want to use.
- Launch the task.
Credentials Reuse Targets
Credentials Reuse utilizes several login scanners from the Metasploit Framework, which enable Credentials Reuse to target the following services: AFP, DB2, FTP, HTTP, HTTPS, MSSQL, MySQL, POP3, PostgreSQL, SMB, SNMP, SSH, telnet, VNC, and WinRM.
Targets that do not have a login scanner, such as DCERPC, will be skipped.
Configuring and Running Credentials Reuse
- From within a project, select Credentials > Reuse.
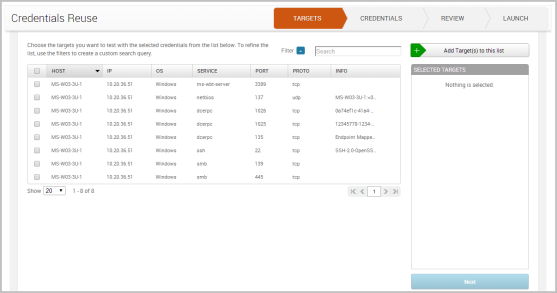
The Credentials Reuse workflow appears. The Targets tab displays first and shows you the targets that are available in the project. Targets, in this instance, are services. Metasploit Pro pulls this data from the host and service data that is stored in the project.
- Select the targets that you want to try the credentials on. You can select as many targets as you want. When you are done selecting targets, click the Add Target(s) to this list button. The targets will be added to the Selected Targets list.
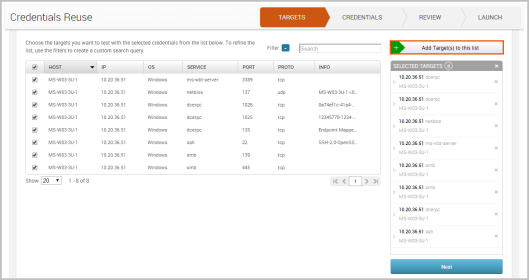
You can use the Select All checkbox to choose all the targets in the project and the page navigation arrows to look through the targets list. If you want to view all targets in the project, select the All option from the Show dropdown menu.
You can also click on the Filter button to find targets based on host, service, port, operating system, protocol, and keyword.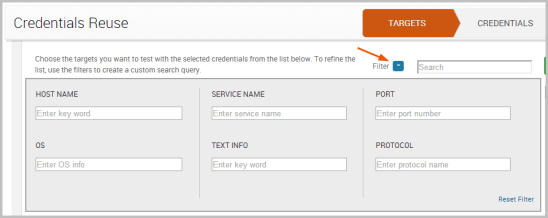
- Click the Next button when you are done selecting targets. The Credentials tab displays and shows you the credentials that are available in the project.
- Select the credentials that you want to reuse. You can select as many credentials as you want. When you are done selecting credentials, click the Add Credential(s) to this list button. The targets will be added to the Selected Credentials list.
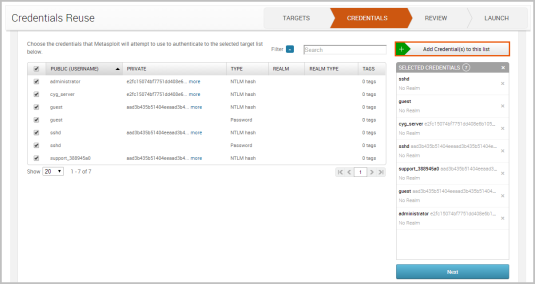
You can use the Select All checkbox to choose all the targets in the project and the page navigation arrows to look through the credentials list. If you want to view all credentials in the project, select the All option from the Show dropdown menu.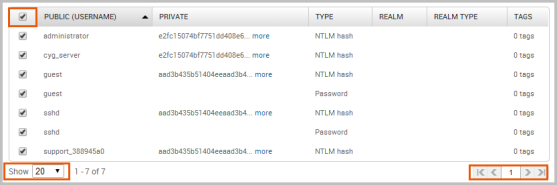
You can also click on the Filter button to find credentials based on validation status, username, password, private type, realm, and tag.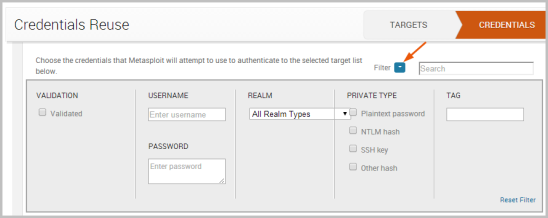
- Select the Next button when you are done selecting credentials. The Review tab appears and shows you the options that you can set for Credentials Reuse and the targets and credentials that you have selected.
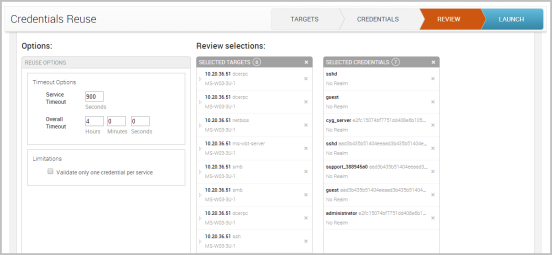
- If you want to control the timeout settings for Credentials Reuse, you can configure any of the following options:
- Service Timeout - Sets the timeout, in seconds, for each target.
- Overall Timeout - Sets the timeout for the entire Credentials Reuse task.
- Validate one credential per service - Limits the number of credentials that are validated for a service on a host to one. Once a credential has been validated for a service, Credentials Reuse will stop testing with other credentials.
- Review the targets and credentials that you have selected for Credentials Reuse.
If there are any that you want to remove, you can click on the Remove 'X' button located next to the target or credential or you can click on the Remove 'X' button located at the top of each list to remove all targets or credentials.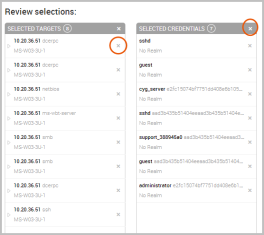
If there are targets or credentials you want to add, you can either click on the tab for the item you want to add or you can click on the Go back and edit link located at the bottom of the Selected Targets and Selected Credentials lists.
If you want to see additional information for a particular target, you can click on the dropdown arrow located next to each target to display the operating system, port, and protocol. - Click the Launch button when you are ready to run Credentials Reuse. There is a launch button located at the top and bottom of the workflow.
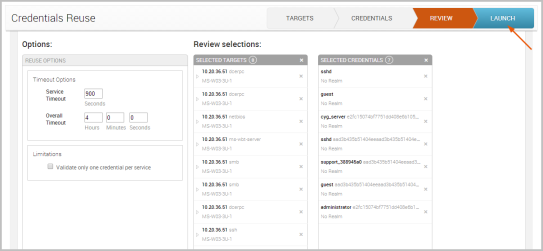
When you launch Credentials Reuse, the Findings window appears and shows you the statistics for the task run. You can click on any of the statistic bubbles to view the details for that particular statistic.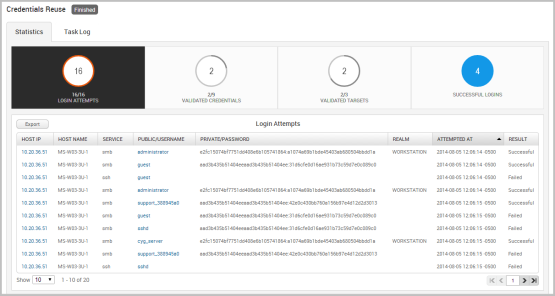
The Findings window shows you the following statistics:
- Login attempts - The total number of login attempts that were made. Credentials Reuse will only attempt logins for the following services: AFP, DB2, FTP, HTTP, HTTPS, MSSQL, MySQL, POP3, PostgreSQL, SMB, SNMP, SSH, telnet, VNC, and WinRM. Therefore, the Login Attempts may not include all of the targets that you have selected. The Login Attempts also shows you results for the login and when the login was last attempted.
- Validated credentials - The total number of credentials that successfully authenticated.
- Validated targets - The total number of targets that were validated.
- Successful logins - The total number of logins that were successful. This number is derived from the number of validated credentials and validated targets.
If Metasploit is able to identify a realm for a credential, it will add the realm information to the credential. You can view the updated credential from the Manage Credentials page.
Related Topics