Adding Event Sources
Collectors communicate with your network servers and gather data from your server logs to produce a dashboard of user activity data for your security analysts.
To ensure complete coverage, take an inventory of your network servers and data logs that you will configure as Event Sources.
| View | Event Sources |
|---|---|
| User details | Microsoft Active Directory, LDAP server logs, Rapid7 Metasploit, Virus scanner, VPN, and Endpoint Monitor |
| Asset details | Microsoft Active Directory security logs and the DHCP server logs, Nexpose, and Endpoint Monitor |
| IP address history | Microsoft Active Directory security logs, DHCP server logs |
| Locations | VPN server logs, Cloud services for example, Cloud services (e.g. AWS, Box.com), and Microsoft ActiveSync |
| Services | DNS server logs, firewall, Web proxy, Cloud service - Box.com, Okta, Salesforce, and the Microsoft ActiveSync servers |
| Incidents | Microsoft Active Directory security logs, DHCP server logs, endpoint monitor, VPN servers (IP address ranges), DNS server logs, Firewall, and the Web proxy |
| Threats | DNS server logs, Firewall, and the Web proxy |
Be sure to identify all of the servers that track user activity on your network and assign them to a Collector. Otherwise, the InsightIDR dashboard may be incomplete, and you will not have access to the data you need to keep your network, and your company's assets, safe.
Set up all of your User Attribution Event Sources before you set up any others. InsightIDR provides step-by-step assistance as you set up your data sources.
Configuring an LDAP event source
- Select Data Collection from the InsightIDR menu.
- Click Add Event Source from the Setup Event Source menu.
- When the Add Event Source page displays, click LDAP.

- Select Windows Collector from the Collector dropdown menu.
- Select Microsoft Active Directory LDAP from the Event Source dropdown menu.
- Check the Timezone box if you want to display only U.S. time zones.

- Select the time zone from the Timezone dropdown menu.
- Enter the server name in the Server field.
- Enter the user domain in the User Domain field.
- Enter the refresh rate (in hours) in the Refresh Rate field.
- Select the Credential from the Credential dropdown menu.
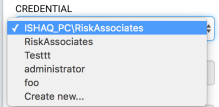
- The Username field automatically populates based on the selected credential.
- The Type field automatically populates based on the selected credential.
- Enter the credential. In this example, the required credential is a password. The field name reflects the credential type.
- Optionally, enter the base distinguished name (Base DN) in the Base DN field.
- Optionally, enter the admin group in the Admin Group field.
- Click the Save button.
LDAP Event Source fields
The LDAP automatically mirrors data across all LDAP servers; thus, even if you have multiple LDAP servers, we only need to configure one LDAP event source (unless you have manually disabled the auto-mirror feature).
Configuring an Active Directory event source
- Click Data Collection from the InsightIDR menu.

- Click Add Event Source from the Setup Event Source menu.

- When the Add Event Source page displays, click Active Directory.

- Select Windows Collector from the Collector dropdown menu.
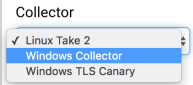
- Select Microsoft Active Directory Security Logs from the Event Source dropdown menu.
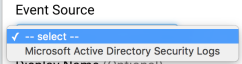
- Check the Timezone box if you want to display only U.S. time zones.

- Select the time zone from the Timezone dropdown menu.

- Click the appropriate Collection Method.
Listening for Syslog
- Select the Protocol from the Protocol dropdown menu.
- Enter the port number in the Port field.
- Click the SAVE button.
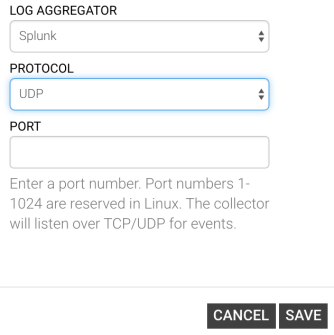
Configuring the Log Aggregator
- Select the Log Aggregator from the Log Aggregator dropdown menu.
- Select the Protocol from the Protocol dropdown menu.
- Enter the port number in the Port field.
- Click the SAVE button.
Configuring WMI
- Enter the server name in the Server field.
- Enter the user domain in the User Domain field.
- Select the Credential from the Credential dropdown menu.

- The Username field automatically populates based on the selected credential.
- Enter the credential. In this example, the required credential is a password. The field name reflects the credential type.
- Click the SAVE button.
Note: AD domain controllers do not mirror data. You'll need to repeat these steps for each domain controller in your environment.
Configuring a DHCP event source
- On your DHCP server, create a new folder for DHCP logs. We recommend placing this folder on the root C drive (C:\dhcplogs).
- Once the folder is created, right-click the folder, select Properties-->Sharing-->Advanced Sharing-->Share this folder-->Permissions-->Add… and provide the credentials that will have access to this file (read-only access is adequate).
- Once the folder is ready, launch the DHCP console and right-click IPv4 in the left pane, then click Properties.
- Under the Advanced tab, change the Audit log file path destination folder to the new folder you just set up (C:\dhcplogs).
- Restart the DHCP server to apply changes.
- From the left panel of the Home page, click Data Collection.
- Select ADD EVENT SOURCE from the SETUP EVENT SOURCE dropdown menu.
- The Add Event Source screen displays. Click DHCP.

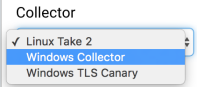
- Select Windows Collector from the Collector dropdown menu.
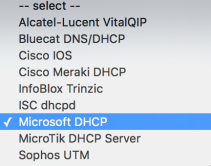
- Select Microsoft DHCP from the Event Source dropdown menu.
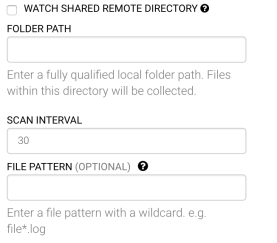
- Click the Watch Directory under the Collection Method.
- Enter the FQDN of the DHCP server and the file path to the folder (C:\dhcplogs).
Configuring other non-Microsoft DHCP sources
- Ensure the DHCP host is logging all DHCP activity.
- Configure DHCP source to send logs to your Collector by specifying it as a syslog server.
- Use the Listen for Syslog Collection Method to ingest logs over a predetermined port.
What's Next?