
Effective use of scan information depends on how your organization analyzes and distributes it, who gets to see it, and for what reason. Managing access to information in the application involves creating asset groups and assigning roles and permissions to users. This chapter provides best practices and instructions for managing users, roles, and permissions.
It is helpful to study how roles and permissions map to your organizational structure.
Note: A user authentication system is included. However, if your organization already uses an authentication service that incorporates Microsoft Active Directory or Kerberos, it is a best practice to integrate the application with this service. Using one service prevents having to manage two sets of user information.
In a smaller company, one person may handle all security tasks. He or she will be a Global Administrator, initiating scans, reviewing reports, and performing remediation. Or there may be a small team of people sharing access privileges for the entire system. In either of these cases, it is unnecessary to create multiple roles, because all network assets can be included in one site, requiring a single Scan Engine.
Example, Inc. is a larger company. It has a wider, more complex network, spanning multiple physical locations and IP address segments. Each segment has its own dedicated support team managing security for that segment alone.
One or two global administrators are in charge of creating user accounts, maintaining the system, and generating high-level, executive reports on all company assets. They create sites for different segments of the network. They assign security managers, site administrators, and system administrators to run scans and distribute reports for these sites.
The Global Administrators also create various asset groups. Some will be focused on small subsets of assets. Non-administrative users in these groups will be in charge of remediating vulnerabilities and then generating reports after follow-up scans are run to verify that remediation was successful. Other asset groups will be more global, but less granular, in scope. The non-administrative users in these groups will be senior managers who view the executive reports to track progress in the company's vulnerability management program.
Whether you create a custom role or assign a preset role for an account depends on several questions: What tasks do you want that account holder to perform? What data should be visible to the user? What data should not be visible to the user.
For example, a manager of a security team that supports workstations may need to run scans on occasion and then distribute reports to team members to track critical vulnerabilities and prioritizing remediation tasks. This account may be a good candidate for an Asset Owner role with access to a site that only includes workstations and not other assets, such as database servers.
Note: Keep in mind that, except for the Global Administrator role, the assigning of a custom or preset role is interdependent with access to site and asset groups.
If you want to assign roles with very specific sets of permissions you can create custom roles. The following tables list and describe all permissions that are available. Some permissions require other permissions to be granted in order to be useful. For example, in order to be able to create reports, a user must also be able to view asset data in the reported-on site or asset group, to which the user must also be granted access.
The tables also indicate which roles include each permission. You may find that certain roles are granular or inclusive enough for a given account. A list of preset roles and the permissions they include follows the permissions tables. See Give a user access to asset groups.
These permissions automatically apply to all sites and asset groups and do not require additional, specified access.
| Permission | Description | Role |
|---|---|---|
| Manage Sites | Create, delete, and configure all attributes of sites, except for user access. Implicitly have access to all sites. Manage shared scan credentials. Other affected permissions: When you select this permission, all site permissions automatically become selected. See Site permissions. | Global Administrator |
| Manage Scan Templates | Create, delete, and configure all attributes of scan templates. | Global Administrator |
| Manage Report Templates | Create, delete, and configure all attributes of report templates. |
Global Administrator, Security Manager and Site Owner, Asset Owner, User |
| Manage Scan Engines | Create, delete, and configure all attributes of Scan Engines; pair Scan Engines with the Security Console. | Global Administrator |
| Manage Policies | Copy existing policies; edit and delete custom policies. | Global Administrator |
| Appear on Ticket and Report Lists |
Appear on user lists in order to be assigned remediation tickets and view reports. Prerequisite: A user with this permission must also have asset viewing permission in any relevant site or asset group: View Site Asset Data; View Group Asset Data |
Global Administrator, Security Manager and Site Owner, Asset Owner, User |
| Configure Global Settings | Configure settings that are applied throughout the entire environment, such as risk scoring and exclusion of assets from all scans. | Global Administrator |
| Manage Tags | Create tags and configure their attributes. Delete tags except for built-in criticality tags. Implicitly have access to all sites. | Global Administrator |
These permissions only apply to sites to which a user has been granted access.
| Permission | Description | Role |
|---|---|---|
| View Site Asset Data | View discovered information about all assets in accessible sites, including IP addresses, installed software, and vulnerabilities. |
Global Administrator, Security Manager and Site Owner, Asset Owner, User |
| Specify Site Metadata | Enter site descriptions, importance ratings, and organization data. |
Global Administrator, Security Manager and Site Owner |
| Specify Scan Targets | Add or remove IP addresses, address ranges, and host names for site scans. | Global Administrator |
| Assign Scan Engine | Assign a Scan Engine to sites. | Global Administrator |
| Assign Scan Template | Assign a scan template to sites. |
Global Administrator, Security Manager and Site Owner |
| Manage Scan Alerts | Create, delete, and configure all attributes of alerts to notify users about scan-related events. |
Global Administrator, Security Manager and Site Owner |
| Manage Site Credentials | Provide logon credentials for deeper scanning capability on password-protected assets. |
Global Administrator, Security Manager and Site Owner |
| Schedule Automatic Scans | Create and edit site scan schedules. |
Global Administrator, Security Manager and Site Owner |
| Start Unscheduled Scans | Manually start one-off scans of accessible sites (does not include ability to configure scan settings). | Global Administrator, Security Manager and Site Owner, Asset Owner |
| Purge Site Asset Data |
Manually remove asset data from accessible sites. Prerequisites: A user with this permission must also have one of the following permissions: View Site Asset Data; View Group Asset Data |
Global Administrator |
| Manage Site Access | Grant and remove user access to sites. | Global Administrator |
These permissions only apply to asset groups to which a user has been granted access.
| Permission | Description | Role |
|---|---|---|
| Manage Dynamic Asset Groups |
Create dynamic asset groups. Delete and configure all attributes of accessible dynamic asset groups except for user access. Implicitly have access to all sites. Note: A user with this permission has the ability to view all asset data in your organization. |
Global Administrator |
| Manage Static Asset Groups |
Create static asset groups. Delete and configure all attributes of accessible static asset groups except for user access. Prerequisite: A user with this permission must also have the following permissions and access to at least one site to effectively manage static asset groups: Manage Group Assets; View Group Asset Data |
Global Administrator |
| View Group Asset Data | View discovered information about all assets in accessible asset groups, including IP addresses, installed software, and vulnerabilities. |
Global Administrator ,
Security Manager and Site Owner, Asset Owner, User |
| Manage Group Assets |
Add and remove assets in static asset groups. Note: This permission does not include ability to delete underlying asset definitions or discovered asset data. Prerequisite: A user with this permission must also have of the following permission: View Group Asset Data |
Global Administrator |
| Manage Asset Group Access | Grant and remove user access to asset groups. | Global Administrator |
The Create Reports permission only applies to assets to which a user has been granted access. Other report permissions are not subject to any kind of access.
| Permission | Description | Role |
|---|---|---|
| Create Reports |
Create and own reports for accessible assets; configure all attributes of owned reports, except for user access. Prerequisites: A user with this permission must also have one of the following permissions: View Site Asset Data; View Group Asset Data |
Global Administrator ,
Security Manager and Site Owner, Asset Owner, User |
|
Use Restricted Report Sections |
Create report templates with restricted sections; configure reports to use templates with restricted sections. Prerequisites: A user with this permission must also have one of the following permissions: Manage Report Templates |
Global Administrator |
| Manage Report Access | Grant and remove user access to owned reports. | Global Administrator |
These permissions only apply to assets to which a user has been granted access.
| Permission | Description | Role |
|---|---|---|
| Create Tickets |
Create tickets for vulnerability remediation tasks. Prerequisites: A user with this permission must also have one of the following permissions: View Site Asset Data; View Group Asset Data |
Global Administrator ,
Security Manager and Site Owner, Asset Owner, User |
| Close Tickets |
Close or delete tickets for vulnerability remediation tasks. Prerequisites: A user with this permission must also have one of the following permissions:View Site Asset Data; View Group Asset Data |
Global Administrator ,
Security Manager and Site Owner, Asset Owner, User |
These permissions only apply to sites or asset groups to which a user has been granted access.
| Permission | Description | Role |
|---|---|---|
| Submit Vulnerability Exceptions |
Submit requests to exclude vulnerabilities from reports. Prerequisites: A user with this permission must also have one of the following permissions: View Site Asset Data; View Group Asset Data |
Global Administrator ,
Security Manager and Site Owner, Asset Owner, User |
| Review Vulnerability Exceptions |
Approve or reject requests to exclude vulnerabilities from reports. Prerequisites: A user with this permission must also have one of the following permissions: View Site Asset Data; View Group Asset Data |
Global Administrator |
| Delete Vulnerability Exceptions |
Delete vulnerability exceptions and exception requests. Prerequisites: A user with this permission must also have one of the following permissions: View Site Asset Data; View Group Asset Data |
Global Administrator |
The Global Administrator role differs from all other preset roles in several ways. It is not subject to site or asset group access. It includes all permissions available to any other preset or custom role. It also includes permissions that are not available to custom roles:
The Security Manager and Site Owner roles include the following permissions:
The only distinction between these two roles is the Security Manager’s ability to work in accessible sites and assets groups. The Site Owner role, on the other hand, is confined to sites.
The Asset Owner role includes the following permissions in accessible sites and asset groups:
Although “user” can refer generically to any owner of aNexpose account, the name User, with an upper-case U, refers to one of the preset roles. It is the only role that does not include scanning permissions. It includes the following permissions in accessible sites and asset groups:
This role provides complete access to ControlsInsight with no access to Nexpose.
The Users links on the Administration page provide access to pages for creating and managing user accounts. Click manage next to Users to view the Users page. On this page, you can view a list of all accounts within your organization. The last logon date and time is displayed for each account, giving you the ability to monitor usage and delete accounts that are no longer in use.
The application displays the User Configuration panel. The process for editing an account is the same as the process for creating a new user account. See Configure general user account attributes.
To delete an account and reassign tickets or reports:
A dialog box appears asking you to confirm that you want to delete the account.
If that account has been used to create a report, or if that account has been assigned a ticket, the application displays a dialog box prompting you to reassign or delete the report or ticket in question. You can choose delete a report or a ticket that concerns a closed issue or an old report that contains out-of-date information.
You can specify attributes for general user accounts on the User Configuration panel.
To configure user account attributes:
Before you can create externally authenticated user accounts you must define external authentication sources. See Using external sources for user authentication.
You can later disable the account without deleting it by clicking the check box again to remove the check mark.
Assigning a role and permissions to a new user allows you to control that user’s access to Security Console functions.
To assign a role and permissions to a new user:
When you select a role, the Security Console displays a brief description of that role.
If you choose one of the five default roles, the Security Console automatically selects the appropriate check boxes for that role.
If you choose Custom Role, select the check box for each permission that you wish to grant the user.
A Global Administrator automatically has access to all sites. A security manager, site administrator, system administrator, or nonadministrative user has access only to those sites granted by a global administrator.
To grant a user access to specific sites:
The new site appears on the Site Access page.
A global administrator automatically has access to all asset groups. A site administrator user has no access to asset groups. A security manager, system administrator, or nonadministrative user has access only to those access groups granted by a global administrator.
To grant a user access to asset group:
The Security Console displays a box listing all asset groups within your organization.
The new asset group appears on the Asset Group Access page.
You can integrate Nexpose with external authentication sources. If you use one of these sources, leveraging your existing infrastructure will make it easier for you to manage user accounts.
Note: The Security Console's Two Factor Authentication is not currently compatible with Active Directory (LDAP) and Kerberos authentication methods. For more information, see Enabling Two Factor Authentication.
The application provides single-sign-on external authentication with two sources:
Note: The Security Console's Two Factor Authentication is not currently compatible with Active Directory (LDAP) and Kerberos authentication methods. For more information, see Enabling Two Factor Authentication.
The application also continues to support its two internal user account stores:
Before you can create externally authenticated user accounts you must define external authentication sources.
To define external authentication sources:
The Security Console displays a box labeled LDAP/AD Configuration.
Note: It is recommended that you enter a fully qualified domain name in all capital letters for the LDAP server configuration. Example: SERVER.DOMAIN.EXAMPLE.COM
Default LDAP port numbers are 389 or 636, the latter being for SSL. Default port numbers for Microsoft AD with Global Catalog are 3268 or 3269, the latter being for SSL.
Note: It is not recommended that you use PLAIN for non-SSL LDAP connections.
Simple Authentication and Security Layer (SASL) authentication methods for permitting LDAP user authentication are defined by the Internet Engineering Task Force in document RFC 2222 (http://www.ietf.org/rfc/rfc2222.txt). The application supports the use of GSSAPI, CRAM-MD5, DIGEST-MD5, SIMPLE, and PLAIN methods.
As the application attempts to authenticate a user, it queries the target LDAP server. The LDAP and AD directories on this server may contain information about other directory servers capable of handling requests for contexts that are not defined in the target directory. If so, the target server will return a referral message to the application, which can then contact these additional LDAP servers. For information on LDAP referrals, see the document LDAPv3 RFC 2251 (http://www.ietf.org/rfc/rfc2251.txt).
To force the application to search within a specific part of the tree, specify a search base, such as CN=sales,DC=acme,DC=com.
Your attribute mapping selection will affect which default values appear in the three fields below. For example, the LDAP attribute Login ID maps to the user’s login ID. If you select AD mappings, the default value is sAMAccountName. If you select AD Global Catalog mappings, the default value is userPrincipalName. If you select Common LDAP mappings, the default value is uid.
The Security Console displays the Authentication page with the LDAP/AD authentication source listed.
To add a Kerberos authentication source:
The Security Console displays a box labeled Kerberos Realm Configuration.
The Security Console displays a warning that the default realm cannot be disabled.
The Security Console displays the Authentication page with the new Kerberos distribution center listed.
Once you have defined external authentication sources, you can create accounts for users who are authenticated through these sources.
The Security Console displays the User Configuration panel.
On the General page, the Authentication method drop-down list contains the authentication sources that you defined in the Security Console configuration file.
Note: If you log on to the interface as a user with external authentication, and then click your user name link at the top right corner of any page, the Security Console displays your account information, including your password; however, if you change the password on this page, the application will not implement the change.
The built-in user store authentication is represented by the Nexpose user option.
The Active Directory option indicates the LDAP authentication source that you specified in the Security Console configuration file.
If you select an external authentication source, the application disables the password fields. It does not support the ability to change the passwords of users authenticated by external sources.
If you are authenticating users with Kerberos, you can increase security for connections to the Kerberos source, by specifying the types of ticket encryptions that can be used in these connections. To do so, take the following steps:
default_tkt_enctypes=<encryption_type encryption_type>
You can specify any of the following ticket encryption types:
Example:
default_tkt_enctypes= aes128-cts-hmac-sha1-96 aes256-cts-hmac-sha1-96
The changes are applied at the next startup.
Global Administrators can customize the password policy in your Nexpose installation. One reason to do so is to configure it to correspond with your organization's particular password standards.
Note: When you update a password policy, it will take effect for new users and when existing users change their passwords. Existing users will not be forced to change their passwords.
To customize a password policy:

Navigating to the password policy configuration
Note: If you do not want to enforce a maximum length, set the maximum length to 0.

Example: This policy is named Test Policy and enforces a minimum length of 8 characters, maximum length of 24 characters, at least one capital leter, at least one numeric value, and at least one special character.
Once the password policy is set, it will be enforced on the User Configuration page.
As a new password is typed in, the items on the list of requirements turn from red to green as the password requirements are met.
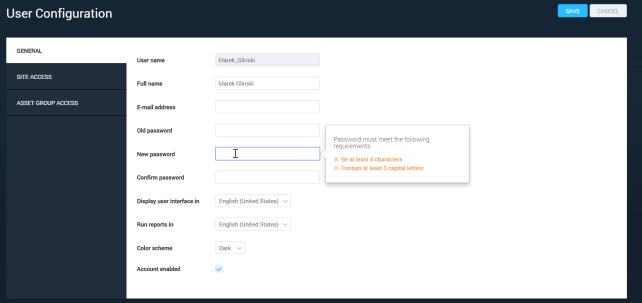
As a user types a new password, the requirements on the list change from red to green as they are fulfilled.
If a user attempts to save a password that does not meet all the requirements, an error message will appear.