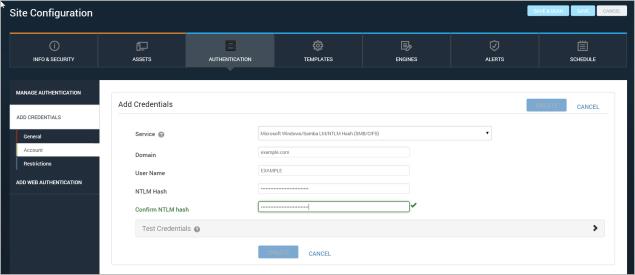
Nexpose can pass LM and NTLM hashes for authentication on target Windows or Linux CIFS/SMB services. With this method, known as “pass the hash,” it is unnecessary to “crack” the password hash to gain access to the service.
Several tools are available for extracting hashes from Windows servers. One solution is Metasploit, which allows automated retrieval of hashes. For information about Metasploit, go to www.rapid7.com.
When you have the hashes available, take the following steps:
If you want to add credentials while configuring a new site, click the Create site button on the Home page.
OR
Click the Create tab at the top of the page and then select Site from the drop-down list.
If you want to add credentials for an existing site, click that site's Edit icon in the Sites table on the Home page.
01FC5A6BE7BC6929AAD3B435B51404EE:0CB6948805F797BF2A82807973B89537
0CB6948805F797BF2A82807973B89537

NTLM hash
For additional optional steps, see the following topics: