Windows PowerShell is a command-line shell and scripting language that is designed for system administration and automation. As of PowerShell 2.0, you can use Windows Remote Management to run commands on one or more remote computers. By using PowerShell and Windows Remote Management with your scans, you can scan as though logged on locally to each machine. PowerShell support is essential to some policy checks in SCAP 1.2, and more efficiently returns data for some other checks.
In order to use Windows Remote Management with PowerShell, you must have it enabled on all the machines you will scan. If you have a large number of Windows assets to scan, it may be more efficient to enable it through group policy on your Windows domain.
Additionally, when using Windows Remote Management with PowerShell via HTTP, you need to allow unencrypted traffic.
To allow unencrypted traffic:
Policies > Administrative Templates > Windows Components > Windows Remote Management (WinRM) > WinRM Service
OR
From a command prompt, run:
winrm set winrm/config/service @{AllowUnencrypted="true"}
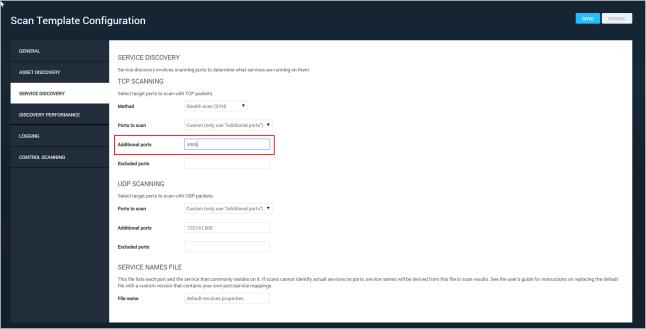
For scans to use Windows Remote Management with PowerShell, port 5985 must be available to the scan template. The scan templates for DISA, CIS, and USGCB policies have this port included by default; for others you will need to add it manually.
To add the port to the scan template:

Adding port 5985
You also need to specify the appropriate service and credentials.
To specify the service and credentials, take the following steps:
If you want to add credentials while configuring a new site, click the Create site button on the Home page.
If you want to add credentials for an existing site, click that site's Edit icon in the Sites table on the Home page.
For additional optional steps, see the following topics:
The application will automatically use PowerShell if the correct port is enabled, and if the correct Microsoft Windows/Samba (SMB/CIFS) credentials are specified.
If you have PowerShell enabled, but don’t want to use it for scanning, you may need to define a custom port list that does not include port 5985.
To disable access to the port: