Getting Started with InsightIDR
InsightIDR monitors authentication activity and provides customizable incidents to track access to sensitive systems and environments deemed important from a security or business perspective. Rules can be tailored to whitelist or blacklist users or user groups and to monitor access to individual assets or entire network ranges. This helps businesses identify unauthorized access from external and internal threats. Furthermore, these controls help enforce both internal and external policy compliance.
InsightIDR is a security tool that begins and ends with the user in mind. It focuses on user accounts that are the most common targets for sophisticated attacks, while most tools focus on assets, executables, or packet signatures. InsightIDR automatically analyzes and correlates user accounts with assets, network activity, and data from other security tools in your environment, looking for irregular behavior and known indicators of compromise. Activity that may be indicative of a breach generates an incident, which contains not only user data, but also the aforementioned asset data so that, in the event of a breach, security teams have a more complete picture of not just what was involved, but who was responsible, when the event happened, and where the intruder is headed next.
InsightIDR allows you to gain control of the vast amount of user activity data available from devices that manage your network. Track the network resources your users are working on, the devices they are using, and even the cloud services they are visiting. If you have concerns about a web site, Web service, or mobile device, you can tell at a glance which accounts are using it.
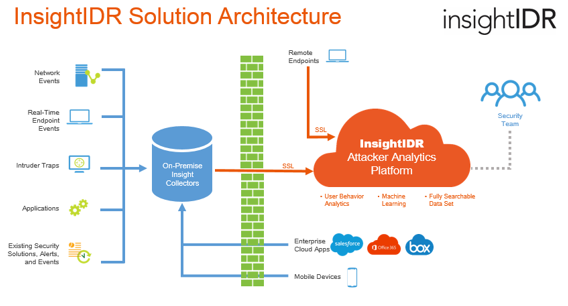
The quality of information available in InsightIDR is determined by the configuration of your data sources.
Collectors aggregate and transmit data from Event Sources to InsightIDR which runs analytics and populates views in the Web application. Event sources provide log data from devices that access your corporate network from anywhere in the world.
In order to obtain access to this log data, the InsightIDR Collector requires domain administrator credentials that have permission to read the Active Directory and Windows Endpoint log files. The InsightIDR Collector is hosted on-premise in the customer's environment, and credentials are never readable anywhere outside the Collector on the corporate network. The log files are passed through a filter before the data is transmitted to ensure that only the most necessary information is uploaded to the hardened InsightIDR backend for analysis.
To prepare your network to work with InsightIDR, identify a server or virtual machine where you will deploy your Collector, and then identify the Event Sources that will provide user activity data from your network.
What's Next?