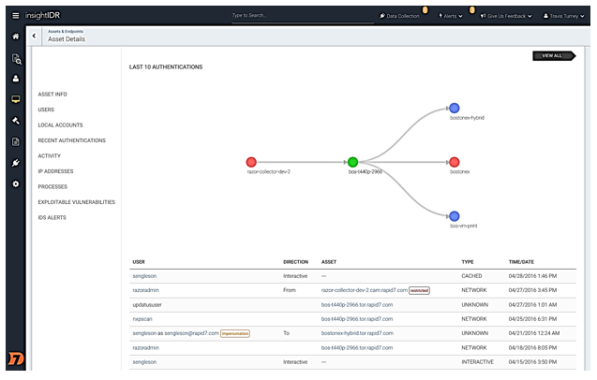
Viewing Lateral Movement
Authentication activity on the endpoint, whether using local or domain accounts, includes the source machine and account from which the authenticator came. With this information, InsightIDR can aggregate and present visualizations displaying exactly where users came from when logging into any particular asset on the network and which assets users authenticated to next from that asset. The following interactive graph provides a quick and easy way for security administrators to retrace the steps of any lateral movement as it hops from machine to machine across the environment. When lateral movement seems particularly excessive, or when it involves a Watchlist or administrator account, an incident is raised to warn the security team of the activity.
Attackers move laterally when they jump from one endpoint to another to infiltrate a network. This is a very common attacker methodology, including pass-the-hash attacks. Lateral movement cannot be detected simply by reading Active Directory logs – it requires visibility into the endpoints.
What's Next?